OpenID Single Sign On
Open ID Setup
PlanSource supports OpenID Connect 1.0 (often referred to as OIDC) We follow the standard protocols and have added additional optional functionality to support SSL Mutual Authentication and the ability to remove a prefix from the claim subject mapping.
Access the Single Sign-On configuration by using the left navigation, select System, and then Single Sign-On
Within the Single Sign-On configuration, enable the SSO Login Access for the admin and/or subscriber roles. You enable them by selecting whether or not they will have to SSO for access or if they will be able to use both SSO & a direct login.
To configure OpenID Connect, select the OpenId tab.
PlanSource employees are the only users that have access to the Client ID & Client Secret fields. You must send the information to your PlanSource support representative to have these fields completed.

Most integrations use the Discover Feature of the OIDC specification and this simplifies configuration.
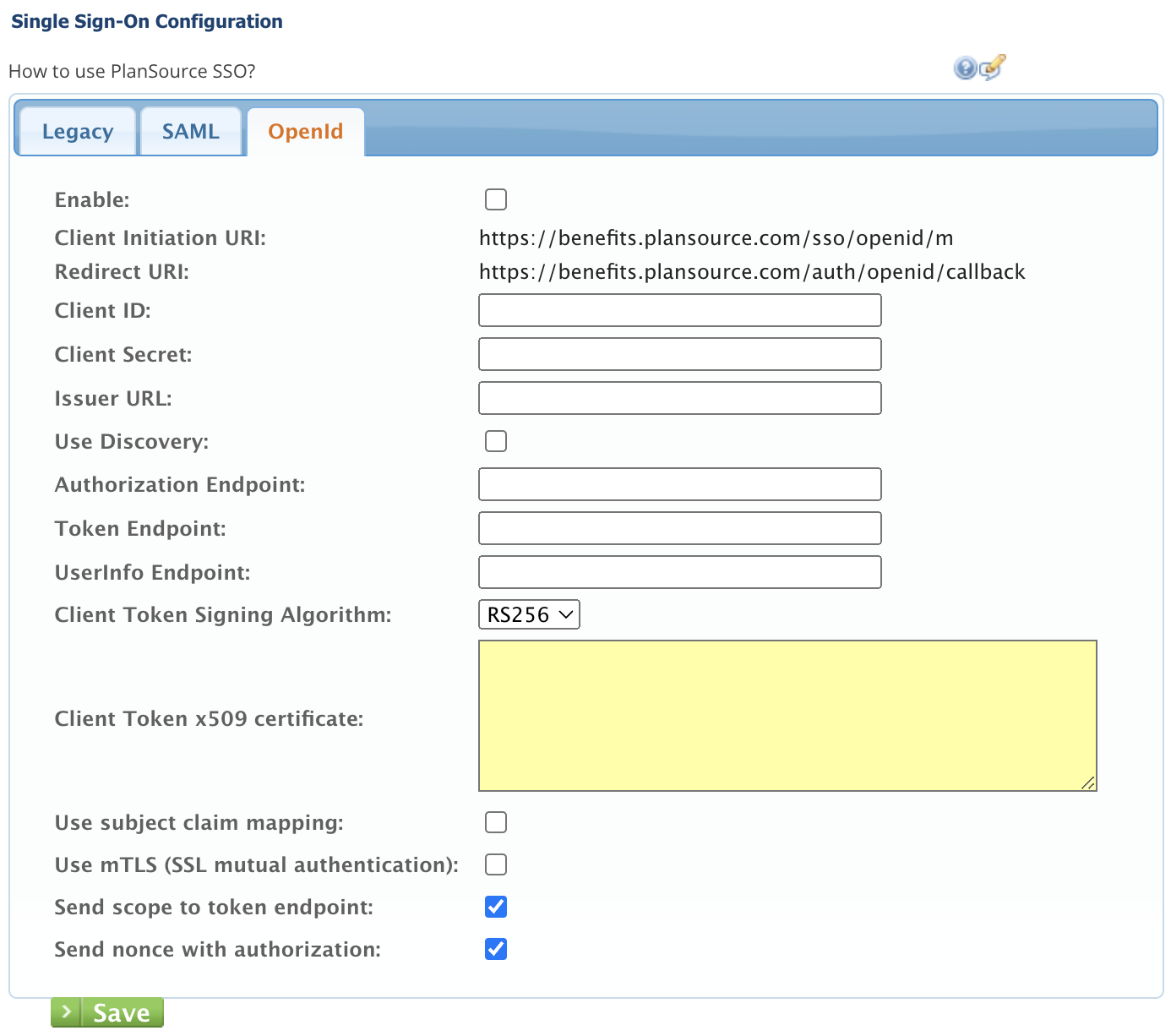
When configuring the OIDC on the iDP system, you will need to enter the Client Initiation URI and Redirect URI. The Client Initiation URI is specific to each environment/organization in PlanSource’s system. The Redirect URI is specific to each environment.
The remaining configuration values should provided from the iDP system.
Issuer URL is defined by the iDP.
Send scope to token endpoint is defined by the iDP.
Send nonce with authorization is defined by the iDP.
To support various clients, we have added the capability to manipulate the subject claim mapping that is sent from the iDP.
For example, when using Salesforce, the subject claim mapping is sent as https://salesforce.com/organization-id/subject-idenifier.
In PlanSource’s system, we map the Subject claim value to the API SSO ID field which is often set through an API invocation or excel import. In our example, the value in the API SSO ID field is usually set to subject-identifier, thus we would not be able to properly identify the users in the two systems.
To resolve this issue, you can enable the Subject Claim mapping and set the modification type to Remove Prefix. The subject claim modification text will perform an exact match of the entered string and remove it from the value that is passed from the iDP in the subject claim mapping data. For our example, the subject claim modification test would be set to https://salesforce.com/organization-id/ thus incoming OIDC would identify the incoming user as subject-identifier and confirm that the user with subject-identifier exist by looking up the API SSO ID field on the employee and/or admin record.
User enablement
Follow the directions on https://developer.plansource.com/docs/configuring-employee-sso-in-plansource to setup each employee mapping.
Within the subscriber api call, you can set the value of the API SSO ID by setting the attribute subscriber_code when creating/updating a subscriber.
Updated 4 months ago
