PlanSource/Okta SAML SSO
Client Companion Guide
Note:
This page is for reference only and may be outdated. You must work with your Okta Representative for configuration support.
Overview
The following is a client guide for setting up a custom SAML SSO outgoing connection from Okta to PlanSource for the employee enrollment experience.
Background
What are the requirements to setup the SAML SSO connection?
Please verify with your PlanSource account manager or implementation project manager to verify all of the following has been done prior to starting the Okta SSO configuration process or if any errors occur with the SSO connection.
- Your client must be fully configured in the PlanSource system.
- Each of your employees in PlanSource must have their Okta email/username stored in the PlanSource API-SSO/Subscriber Code.
- You must have administrator access to Okta to add applications, configure those applications, and assign applications to users.
- You must have administrator access to PlanSource and have logged in at least once to the PlanSource administrator page to accept the EULA before any employee can SSO.
- Okta must be the only inbound SSO configuration you will be using with PlanSource. PlanSource does not support incoming SSO from multiple vendors.
Disclaimer
This is a PlanSource generated client guide to walk you through the configuration settings PlanSource uses and how Okta can be configured as of today (11/10/17). PlanSource and Okta do not have an official SAML SSO option available. This document has been reviewed and tested, but please note that PlanSource is not responsible for changes made to the Okta system, service, or accuracy of the screenshots within this document. PlanSource cannot guarantee that this guide will facilitate a successful SAML SSO connection.
Configuration Details
Connection Information
| Okta Configuration Items | Client Information |
|---|---|
| Single Sign On URL: | https://benefits.plansource.com/sso/employee/saml2/post/ |
| Audience URI (SP Entity ID): | https://benefits.plansource.com |
| Default Relay State: | Client Specific - PlanSource to Provide |
| Name ID Format: | Unspecified |
| Application Username: | Okta username |
Advanced Settings
| Okta Configuration Items | Client Information |
|---|---|
| Response: | Signed |
| Assertion Signature: | Signed |
| Signature Algorithm: | RSA-SHA256 |
| Digest Algorithm: | SHA256 |
| Assertion Encryption: | Unencrypted |
| Enable Single Logout: | Optional |
| Authentication Context Class: | PasswordProtectedTransport |
| Honor Force Authentication: | Yes |
| SAML Issuer ID: | http://www.okta.com/${org.externalKey} |
Attribute Statements
| Name | Name Format | Value |
|---|---|---|
| empID | Unspecified | user.email |
Steps & Processes
Please ensure all documents relating to this SSO configuration are sent via SECURE EMAIL ONLY!
Create a Custom PlanSource Application in Okta
This section details how to create a custom application in Okta.
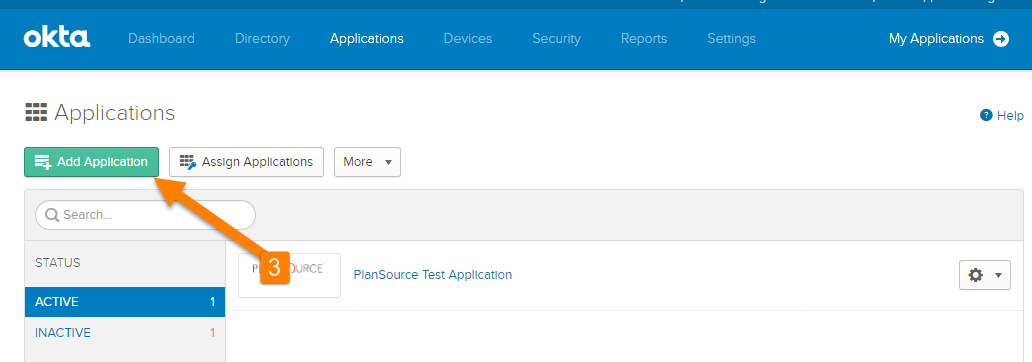
- Access the Okta application as an administrator.
- Navigate to the application section within Okta.
- Then click on the available button to [Add Application].
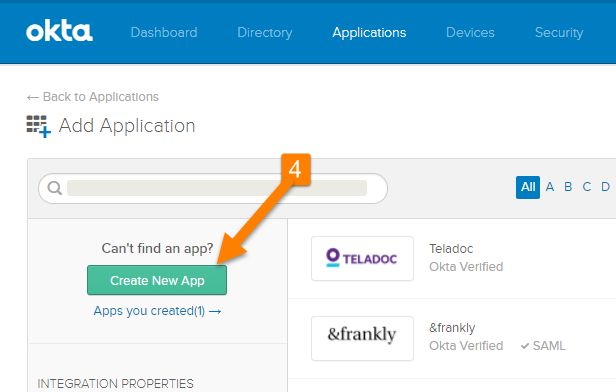
- Click on the button to [Create New App].
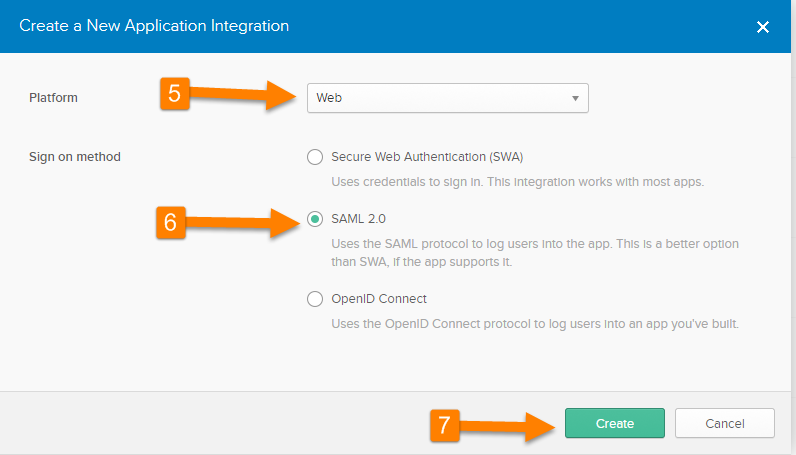
- Set the platform setting to [Web].
- Set the sign on method to be [SAML 2.0].
- Click on [Create].
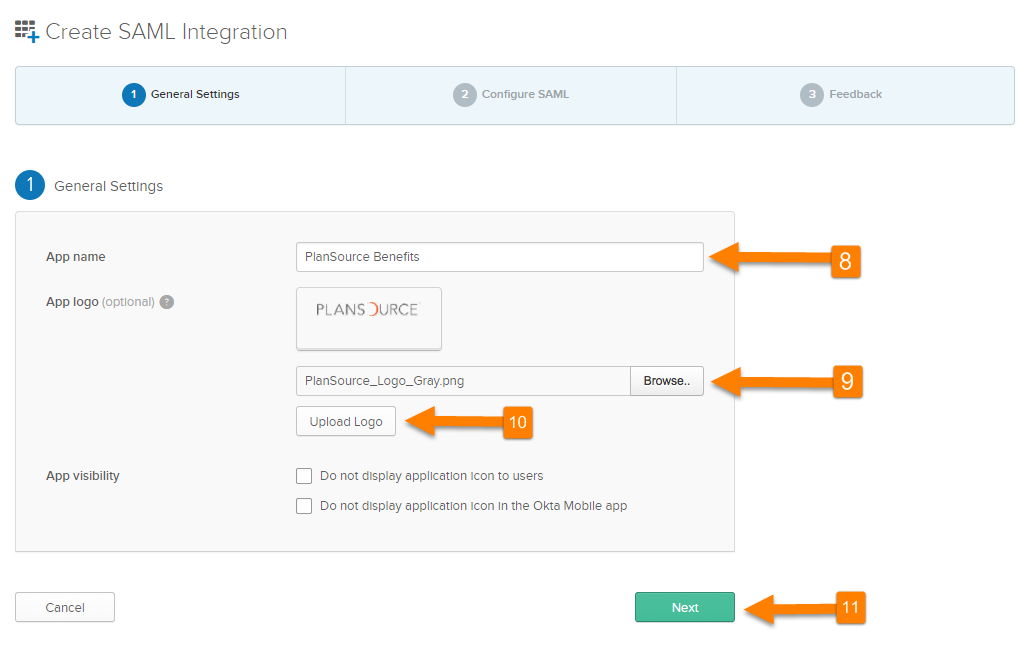
- Enter the App name as “PlanSource Benefits”.
- Use [Browse] to select the saved logo file that was provided.
- Click on [Upload Logo].
- Click on [Next].
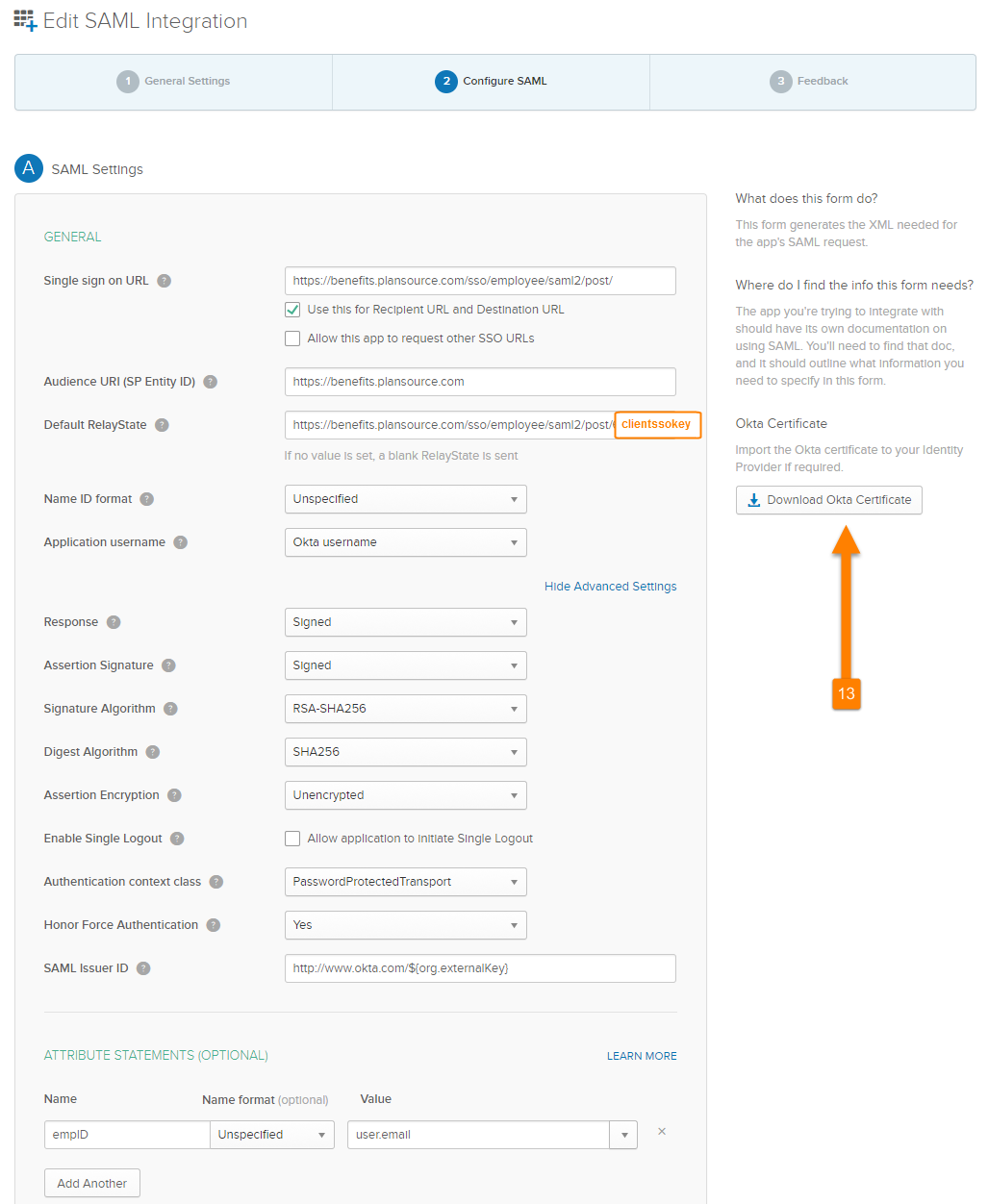
- Complete the configuration page using the information provided in the table contained in this document.
- Click on [Download Okta Certificate] and provide to PlanSource via SECURE EMAIL!
- The last step of the configuration is to add/assign your employees/users to the application to grant them access.
PlanSource Configuration
This section details what information PlanSource will need to allow Okta to connect.
- PlanSource will need the Okta certificate from step 13 above. Please provide this to your account manager and/or implementation resources at PlanSource.
- PlanSource will need a complete list of all active employees with their Okta usernames (typically Okta email) in order to import this data to the API-SSO subscriber code in PlanSource.
Updated 4 months ago
